Twitter’s “Don’t Click” prank, explained
[This information originally appeared here, where I also included an inert copy of the attack code.]
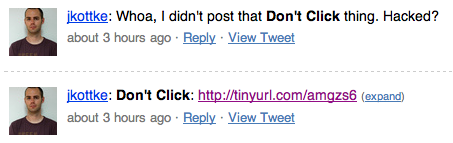
Fig. 1. A common sequence of tweets this morning.
Quick explanation of today’s “Don’t Click??? attack
This viral Twitter prank uses a pretty standard
trick to get you to post something to Twitter, using no JavaScript and only a very little bit of CSS. It requires only that you’re first logged in to twitter.com
(and that your browser’s fonts are pretty close to
standard so that things line up correctly).
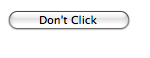
Fig. 2. The “Don’t Click” page.
The attack page creates a button labeled “Don’t Click” that does nothing at
all, but it also loads twitter.com in an
<IFRAME> directly on top of the button. That
IFRAME is then made completely transparent using CSS.
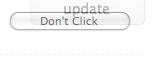
Fig. 3. The hidden IFRAME, exposed.
When you click the button, you’re actually clicking on the (now invisible) ‘Update’
button on Twitter’s web interface instead; assuming you’re logged in
to Twitter, you’ll immediately post whatever’s in the form input box.
Thanks to Twitter’s ?status= URL feature (that allows Twitter
to be pre-loaded with a message), it’s very easy for the attacker to
drop the following message in:
Don’t Click: http://tinyurl.com/amgzs6
That TinyURL expands to http://www.umoor.eu/blog/yes-we-can.php, the
attack page; in this way your followers are also enticed to propagate
the “attack” (which has proven
quite successful).
No accounts were compromised by this prank; you
don’t need to change your Twitter password.
For more information, check out the source to this page, which
includes the attack (but makes the Twitter IFRAME partially visible so
you can see it; it also puts another <DIV> on top
of it to protect you from accidentally clicking the “Submit” button).
See also: an explanation (en Français) by the author of this attack, originally launched in January 2009. (There is some speculation that the code was taken directly from James Padolsey’s proof-of-concept, owing to the similarity of the code.)
As of 1:40PM EST, twitter.com is using some
JavaScript to try to detect when it’s being loaded in an
IFRAME:
if (window.top !== window.self) {
window.top.location.href
= window.self.location.href; }
If you try to load Twitter in an IFRAME you’ll find the
browser
redirected to Twitter automatically (in this case, you’ll
never have an opportunity to click on “Don’t Click”).
I’ve therefore removed the attack from this page, but you can still see
it if you view source.
